Protests in the Age of OSINT
A Shifting Dynamic between Demonstrators and Law Enforcement

On January 6, 2021, America’s eyes were on the Capitol. And, as protesters breached the building, so were thousands of phone cameras.
Armed with their mobile devices, witnesses, staffers, congresspeople, and protesters themselves became “sensors, pointing at this moment,” said Kevin Reyes, senior open-source intelligence specialist at the Institute for Strategic Dialogue (ISD).

Rioters clash with police in Washington, D.C. as they storm the US Capitol on January 6, 2021. | Roberto Schmidt/AFP via Getty Images
Rioters clash with police in Washington, D.C. as they storm the US Capitol on January 6, 2021. | Roberto Schmidt/AFP via Getty Images
The open-source information collected from January 6 became an elaborate body of evidence that ultimately served as the basis for the largest criminal investigation in U.S. history.
This digital evidence, also known as open-source intelligence, or OSINT, allowed law enforcement to identify and charge nearly 90 percent of defendants—known today as “January Sixers”—according to Reyes in an article for ISD.

Pro-Trump protesters gather in front of the Capitol on January 6, 2021, including Proud Boys leader Joe Biggs (C, in plaid). | Jon Cherry/Getty Images
Pro-Trump protesters gather in front of the Capitol on January 6, 2021, including Proud Boys leader Joe Biggs (C, in plaid). | Jon Cherry/Getty Images

Protesters gather in central Hong Kong in June 2019 to protest the China-backed extradition plan, shining lights from their mobile phones. | Kyle Lam/Bloomberg via Getty Images
Protesters gather in central Hong Kong in June 2019 to protest the China-backed extradition plan, shining lights from their mobile phones. | Kyle Lam/Bloomberg via Getty Images
Two years earlier and nearly 10,000 miles away, the impact of OSINT was also felt throughout the pro-democracy protests that shook Hong Kong in 2019.
Just as these protesters risked being identified through their digital footprint, they used these same open-source tools to identify and track law enforcement.
OSINT both powered the January 6 investigation and enabled pro-democracy protesters in Hong Kong to keep tabs on police movement. Its rise is transforming the way people protest in the modern era.
Critically, while open-source information can allow protesters to organize en masse and avoid a physical confrontation with law enforcement, it also may land them behind bars.
As law enforcement and protesters adjust to the increasing importance and availability of open-source information, the landscape of civil unrest is changing.
What is OSINT?

OSINT Glossary of Terminology
▶
Open-Source Intelligence (OSINT)
Intelligence produced by collecting, evaluating and analyzing publicly available information with the purpose of answering a specific intelligence question. While OSINT lacks a formal definition, the United States Intelligence Community defines the term as "intelligence derived exclusively from publicly or commercially available information that addresses specific intelligence priorities, requirements, or gaps." When used by cyber defenders, the goal is to discover publicly available information related to their organization that could be used by attackers, and take steps to prevent those future attacks.
▶
Surveillance
Surveillance is the act of observing another in order to gather evidence. Surveillance is one of the most common methods law enforcement officials use to investigate suspects and gather evidence. Government surveillance is the process of collecting information by a country's government for intelligence, threat monitoring and recognition, prevention and investigation of criminal activity, political information, or social control.
▶
Digital Media Footprint
Sometimes called a digital shadow or an electronic footprint – refers to the trail of data you leave when using the internet. It includes websites you visit, emails you send, and information you submit online. A digital footprint can be used to track a person's online activities and devices. Internet users create their digital footprint either actively or passively.
▶
Civil Unrest
'Civil unrest' is an umbrella term for a wide spectrum of phenomena, and although there is no commonly agreed United Nations definition the term is used widely among United Nations agencies, funds and programs, particularly to describe violent and non-violent group acts.
▶
FOIA
Since 1967, the Freedom of Information Act (FOIA) has provided the public the right to request access to records from any federal agency. It is often described as the law that keeps citizens in the know about their government. Federal agencies are required to disclose any information requested under the FOIA unless exempt.
▶
Public Domain
The term "public domain" refers to creative materials that are not protected by intellectual property laws such as copyright, trademark, or patent laws.
While OSINT lacks a formal definition, the U.S. Intelligence Community defines the term as “intelligence derived exclusively from publicly or commercially available information that addresses specific intelligence priorities, requirements, or gaps.”
OSINT can range from photos on Facebook uploaded by individual users to state-controlled Chinese newspapers.
James A. Lewis, senior vice president, Pritzker Chair, and director of the Strategic Technologies Program at the Center for Strategic and International Studies (CSIS), recalled the evolution of OSINT within the past decade as a “voyage of discovery.”
“People didn’t start out by saying ‘I want to embed information so you can collect it.’ Someone thought it was a good idea to put a timestamp and date and location on your photos . . . a lot of these things grow out of commercial activities, things that seem quite reasonable,” Lewis said.
The end result is a digital trail, from an IP address to digital photos, that follows most individuals in a heavily digitized world. OSINT has evolved with technology.
OSINT and Law Enforcement
Historically, law enforcement has utilized OSINT methods to gather evidence while conducting investigations.
What began as a standard protocol in international courts following major crises like the annexation of Crimea and the war in Syria, Reyes said, is now being applied in domestic law. When it comes to OSINT, nothing in the public domain is off limits.
According to a 1947 document from the Central Intelligence Agency, OSINT made up around 80 percent of all intelligence activities carried out by law enforcement and Western intelligence services.
A 2023 study found that this 80 percent figure still holds true today, demonstrating that gathering intel through OSINT is not new.
What is more recent is the rise in prosecutions globally using evidence gathered through OSINT, according to AI expert Michael Frank, the CEO and cofounder of Seldon Strategies.
“At the end of the day, if investigators have access to open-source information that is lower cost, it's more accessible than trying to get a warrant for the same information that might be just as convincing to a jury,” Frank said.

The Metropolitan Police in Croydon, South London deploy the use of live facial recognition technology to tackle crime and identify offenders. | Jordan Pettitt/PA Images via Getty Images
The Metropolitan Police in Croydon, South London deploy the use of live facial recognition technology to tackle crime and identify offenders. | Jordan Pettitt/PA Images via Getty Images
This accessibility fueled both the prosecution of insurrectionists in the United States and the organization of pro-democracy protesters in Hong Kong. Born out of starkly different political contexts, both incidents reveal the growing influence of open-source information on demonstrations globally.
The January 6 Insurrection

The thousands of public “sensors” documenting the Capitol breach provided a forensic picture of “what actually happened on that day,” Reyes said. “That’s why it was such a watershed moment.”
The amount of evidence publicly available online was a “slam dunk” for law enforcement, Reyes said. But before law enforcement uncovered the identities of these January Sixers, many internet users beat them to the punch, linking online images to names and identities.
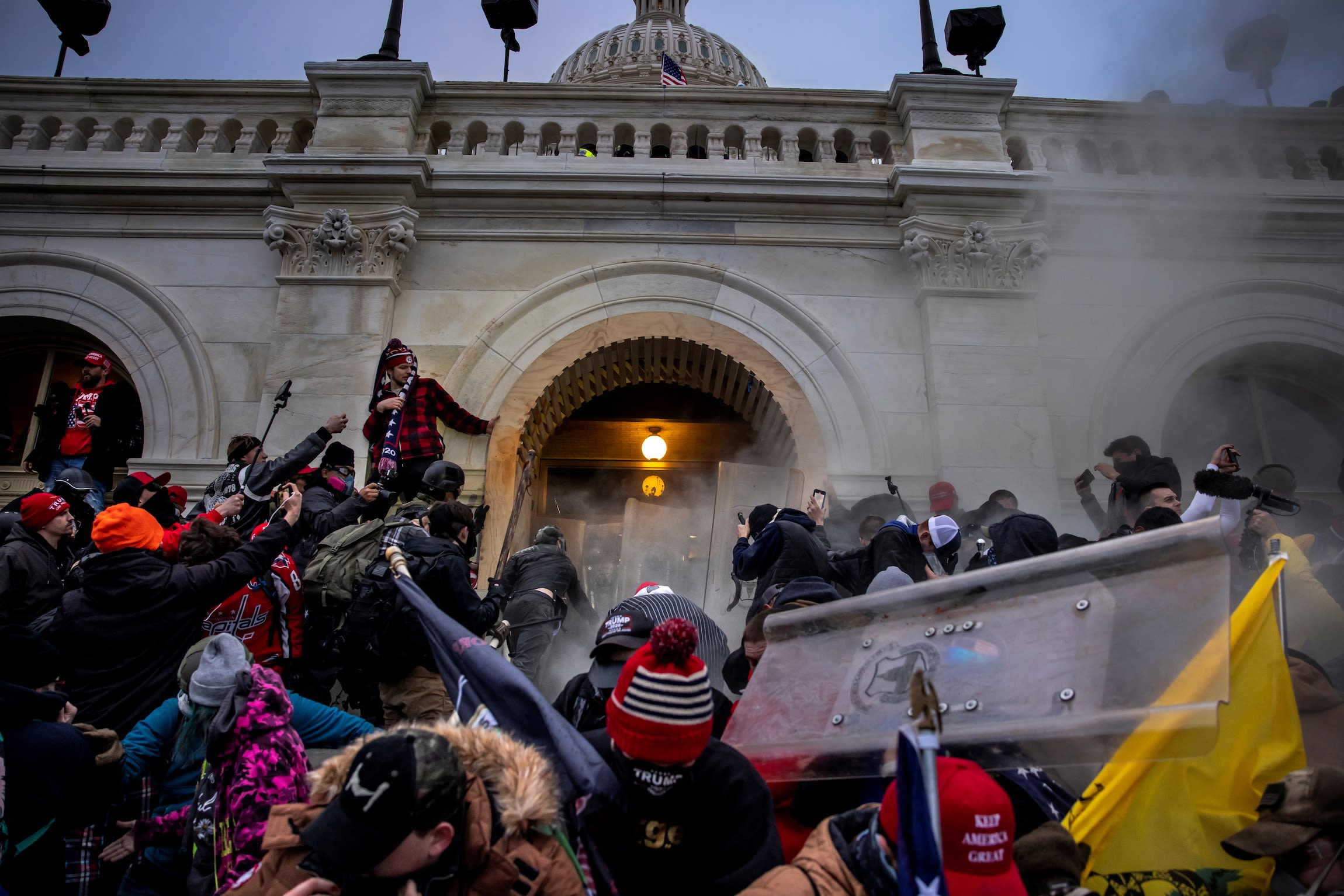


While the responsibility of actually enforcing laws does fall on the officials charged with this task, Reyes emphasized that “the first responders in this incident were members of the general public.”
Open-source evidence appeared in charging documents, court records, and even the final report of the congressional select committee investigating the January 6 attack.
For example, the committee documented how the Proud Boys “led the attack, penetrated the Capitol and led hundreds of others inside,” citing evidence like group leader Enrique Tarrio posting “What if we invade it?” on Telegram, an encrypted social media site.
Inside a Citizen-Led Investigation
Outside of these official documents, citizen investigators formed groups like Sedition Hunters, who according to their website are a “global community of open-source intelligence investigators (OSINT) working together to assist the U.S. FBI and Washington D.C. Capitol Police in finding people who allegedly committed crimes in the January 6 Capitol riots.”
As this community sought to identify suspects through open-source information, insurrectionists were given temporary nicknames, such as “#DeviousDumbledore,” “#FullFlagSuit” and #“TackyTrumpGlasses.”
Each unidentified protester has been given a page where basic information about their involvement in the riots is provided, alongside additional multimedia elements.

Insurrectionists protest inside the Capitol Building after breaching security on January 6, 2021. | Saul Loeb/AFP via Getty Images
Insurrectionists protest inside the Capitol Building after breaching security on January 6, 2021. | Saul Loeb/AFP via Getty Images

A video filmed on January 6 is played for the House Select Committee on the January 6 insurrection in June 2022 in Washington, D.C. | Anna Moneymaker/Getty Images
A video filmed on January 6 is played for the House Select Committee on the January 6 insurrection in June 2022 in Washington, D.C. | Anna Moneymaker/Getty Images
OSINT in the Courts
Sedition Hunters also keeps track of who has been identified and arrested, such as Donald Hazard, formerly #TacklingDummy.
According to records from the Department of Justice, Hazard was arrested in December 2021 on numerous charges including an “act of physical violence in the Capitol Building.”
The Texas man was ultimately sentenced to 57 months in prison for "assaulting, resisting or impeding certain officers," according to the department.
Among the evidence brought to support this charge in court were several examples of open source information found online. According to court records, the FBI requested the public’s assistance in identifying Hazard.
A “tipster” alerted the FBI that Hazard had posted videos of himself on his Facebook account breaking into the Capitol and encouraging others to help “storm the building like a true patriot.”
A Watershed Moment
“If you pore through the criminal complaints, you’ll see that law enforcement relied so much on the work that was already done by the other first responders that I’m talking about,” Reyes said, “which is journalists, civil society, organizations, just general people that were really interested in preserving this moment in time.”
With so much information available online that can identify an individual, Reyes explained that much of law enforcement’s job is just to corroborate this information, put it into a criminal complaint and sign an affidavit saying they believe the information to be true.
This new collaboration between law enforcement and the public made January 6 a watershed moment for the use of OSINT as legal evidence.
Contrarily, OSINT has been used as a weapon against law enforcement, specifically amongst protesters in Hong Kong.
The 2019 Hong Kong Protests

In June 2019, tens of thousands of pro-democracy protesters took to the streets in protest of the Hong Kong government’s proposed extradition bill, which would allow the extradition of criminal cases to mainland China.
The move was perceived as undermining the independence of both Hong Kong’s legal system and its citizens. As a result, pro-democracy protesters quickly mobilized and initiated the first of several pro-democracy protests throughout the year.



Protesters Take on OSINT
Unlike the 2014 peaceful protests known as the Umbrella Movement, protesters experienced a new level of police brutality during the 2019 protests. The government’s response forced protesters of all ages to mobilize, harnessing open-source information.
Former Hong Kong student activist Sunny Cheung said that the police “tried to use excessive force at the very beginning in 2019.” The fatalities that year were unprecedented, Cheung added. The protesters were “forced” to capitalize on OSINT “to ensure there will be some leeway for them to survive,” he said.
Hong Kong’s pro-democracy protesters utilized OSINT to track law enforcement movements in real time. “We helped each other by a simple app . . . It kind of is the only way for you to understand whether or not you are surrounded by the police . . . Otherwise they will arrest you,” said Cheung.
OSINT on the Ground
During the 2019 Hong Kong protests, the extensive use of OSINT by protesters was crucial for ensuring their safety. Apps such as Telegram and HKmap.live helped protesters evade law enforcement and document police misconduct during protests.
Organizations like OSINT HK played a major role in identifying police officers.
For example, in 2019, OSINT HK released a synchronized video to verify that a policeman shot a rubber bullet and blinded Indonesian journalist Veby Indah in her right eye.
The new ability to track and identify law enforcement wrongdoings during protests gave protesters a new level of protection, defense, and courage to participate in the 2019 pro-democracy protests.

This photo illustration shows a smartphone displaying the "HKmap.live" app in Hong Kong on October 10, 2019. | PHILIP FONG/AFP via Getty Images
This photo illustration shows a smartphone displaying the "HKmap.live" app in Hong Kong on October 10, 2019. | PHILIP FONG/AFP via Getty Images

Bridgefy Co-Founder Jorge Rios participates in the Startup Battlefield Competition during TechCrunch Disrupt SF 2017 at Pier 48 on September 18, 2017 in San Francisco, California. | Steve Jennings/Getty Images for TechCrunch
Bridgefy Co-Founder Jorge Rios participates in the Startup Battlefield Competition during TechCrunch Disrupt SF 2017 at Pier 48 on September 18, 2017 in San Francisco, California. | Steve Jennings/Getty Images for TechCrunch
Nonetheless, an additional concern was the inability for protesters to safely communicate with each other due to crowded cell networks and potential online surveillance. The immediate solution was to communicate via Bluetooth apps such as Bridgefy.
The Bluetooth Bridgefy app became increasingly popular as a method to safely stay in touch with other protesters. It allowed users to “stay anonymous” while “[discussing] their operation and tactics,” Cheung said.
The app also allowed users to share information without an internet connection.
Protesters could use OSINT to “inform each other, notify each other, and then decide to withdraw in real time. And I think this is quite smart.” said Cheung.
A Tool and a Weapon

While the identification and prosecution of hundreds of insurrectionists on January 6 highlights law enforcement’s ability to harness open-source information, the strategic organization of pro-democracy protesters in Hong Kong reveals the power of OSINT as a tool for private citizens as well.
The legal and political climate that a protester is operating in is critical to understanding the OSINT methodology at play.

A surveillance device is installed in the Huangpu district of Shanghai, China in May 2024. | Costfoto/NurPhoto via Getty images
A surveillance device is installed in the Huangpu district of Shanghai, China in May 2024. | Costfoto/NurPhoto via Getty images
An Unbalanced Power Dynamic
Through an aggregation of social media information, protesters in Hong Kong were able to track police, just as police were tracking them.
But as Alexa Koenig, co-faculty director of the Human Rights Center at the University of California Berkeley School of Law, points out, the power dynamics between law enforcement and protesters are still unbalanced.
“The police have so much government power behind them,” Koenig said. The idea that one photo taken by a bystander could make someone a police target has led protesters to attempt to mask their identities in the physical world and minimize personal information in the digital world, according to Koenig.
In an era where everyone has a digital footprint, it’s critical for investigators to be cautious about their methodologies in using this powerful new tool. OSINT can form the basis of a criminal prosecution that advances justice or an arbitrary arrest used to quell pro-democracy movements.
Koenig emphasized that open-source investigations “can be used like any tool—in ways that build up communities, and in ways that tear them down.”
Toeing a Fine Line
“When you’re talking about authoritarian or other regimes, what you usually will see is some kind of facade of maybe pretending to be adhering to the rule of law,” Koenig said.
“A really important mantra to keep in mind is that one person’s ‘doxxing’ is another person’s transparency,” Koenig said. This is why a digital source investigator, whether a police officer or private citizen, needs to remember their own positionality.
When pro-democracy protesters in Hong Kong were targeted by the government, this is an example of the kind of overreaching Koenig referenced. But overreaching can also look like a social media user incorrectly identifying a January 6 insurrectionist.
What Does OSINT Mean for the Modern Era of Protests?

OSINT’s integration into law enforcement has far-reaching implications, changing how both law enforcement officials and protesters approach the issue of political dissent.
With more information available online than ever before, protesters are making efforts to conceal their identity, both digitally and in the physical world. Even on American college campuses, where many students are protesting the war in Gaza with concealed faces, anonymity is often impossible to achieve.
“Protesters have sought, like everyone, to limit their digital footprint, but it’s just going to be harder and harder to do,” Lewis said. “People can’t help themselves but post stuff online that leads back to them. Not everybody, but enough that you’re going to have digital footprints.”
“I don’t see people becoming ever disciplined enough to avoid that,” he said.
For law enforcement officials, OSINT will only make identification easier through the gathering of biometric data like collecting voice and facial recognition. While these tools are useful in combating crime, OSINT is also a dual-edged sword posing a myriad of ethical concerns, ranging from freedom of expression to issues of digital privacy. In the face of such ethical concerns, law enforcement will need to reckon with questions of transparency in its use of OSINT.
But, in addition to generating fear of being identified, open-source information can also bring people together as a source of hope.
“The biggest impact has been a sense that no one’s alone,” Koenig said, “that there is a window into worlds that we have never had access to before.”
While risky, this increased online exposure has allowed protesters to organize effectively and share their message with a larger, global audience.
And a watching world is presented with an opportunity to become more engaged in political processes than ever before, as investigators behind a screen.

Authors
Special Thanks:
Story: Marla Hiller
Video: David Lotfi
Audio: Cera Baker
Data: Fabio Murgia
Editorial: Mark Donaldson









